What happened
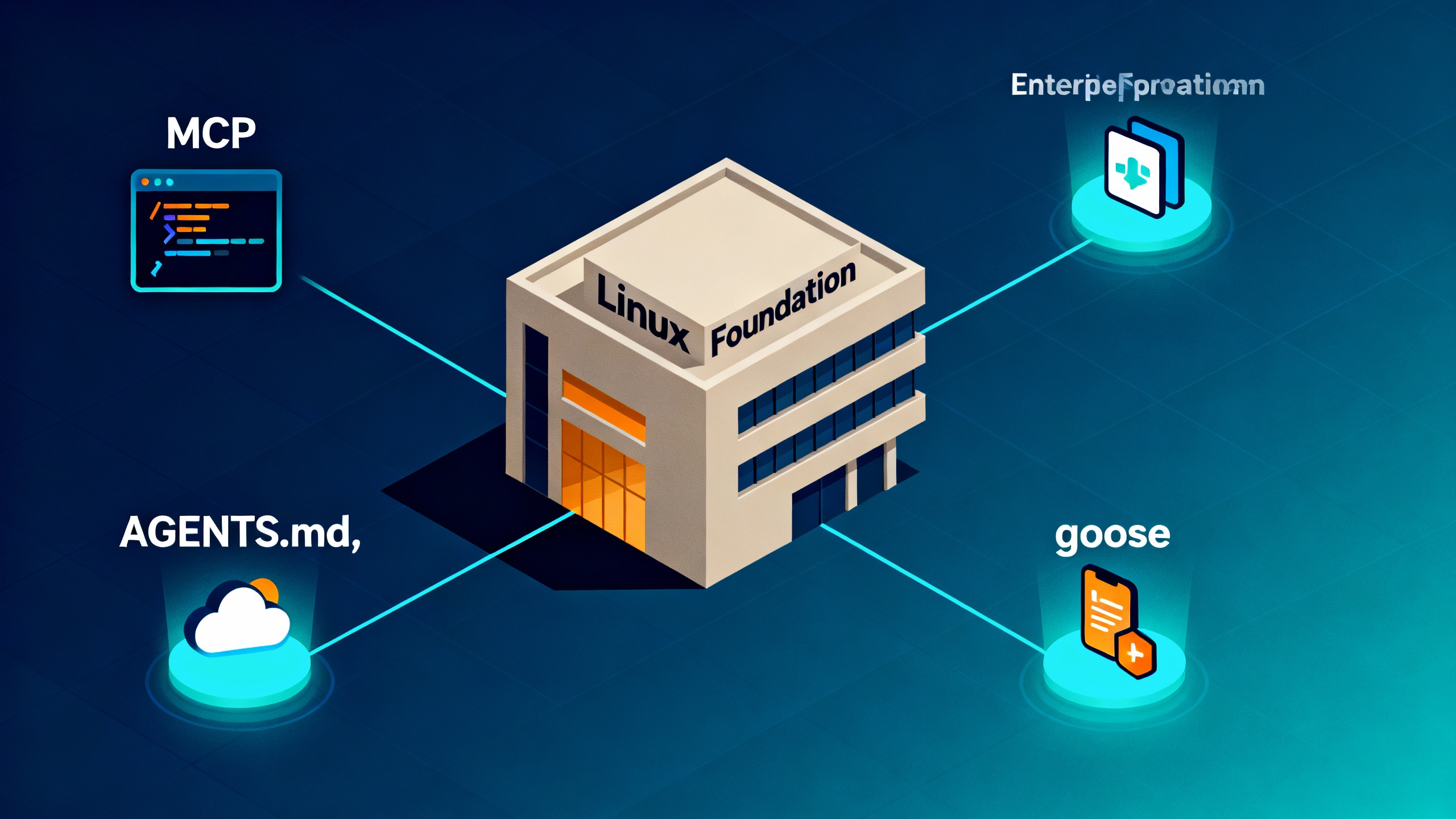
On December 9, 2025, the Linux Foundation announced the Agentic AI Foundation (AAIF) — co‑founded by OpenAI, Anthropic, and Block — as a neutral home for open standards that make AI agents interoperable across vendors and platforms. As part of the launch, the three organizations donated Anthropic’s Model Context Protocol (MCP), OpenAI’s AGENTS.md, and Block’s goose agent framework. The effort operates as a Linux Foundation directed fund and has initial backing from Google, Microsoft, AWS, Bloomberg, and Cloudflare.
Why this matters for automation and productivity
AI agents are moving from demos to deployment, but real productivity gains hinge on common ways for agents to understand projects, talk to tools, and cooperate with each other. MCP tackles the long‑standing “N×M” integration problem by standardizing how agents connect to data sources and services, while AGENTS.md gives coding agents a predictable, portable place to find project‑specific instructions. Donating these to AAIF puts them under neutral governance, reducing lock‑in and aligning incentives around open interoperability.
Beyond these first components, AAIF sits alongside other Linux Foundation efforts aimed at agent interoperability. In 2025 the foundation also introduced Agent2Agent (A2A) for secure agent‑to‑agent communication and welcomed the AGNTCY project for discovery, identity and messaging among heterogeneous agents — signaling a broader “Internet of Agents” stack taking shape in open source.
What’s in the starter pack
Foundational projects donated to AAIF
| Component | Donated by | What it is | Why it matters |
|---|---|---|---|
| Model Context Protocol (MCP) | Anthropic | Open standard for connecting agents/models to external tools, data and apps | Unifies how agents securely access real‑world systems; already supported across major products and clouds |
| AGENTS.md | OpenAI | Simple, open Markdown convention for repository‑level instructions to coding agents | Makes agent behavior more predictable across repos, tools and IDEs; portable and vendor‑neutral |
| goose | Block | Local‑first, open‑source agent framework that executes multi‑step workflows and integrates with MCP | A practical reference agent for building and running automations on‑device or via CLI |
MCP has seen rapid adoption over the past year — with 10,000+ active public servers and support across ChatGPT, Cursor, Google’s Gemini, Microsoft Copilot, and Visual Studio Code — while OpenAI reports more than 60,000 open‑source projects and frameworks now include AGENTS.md. Goose remains fully open‑source and MCP‑compatible, giving teams a concrete starting point to build and test agent workflows.
How it fits with the Linux Foundation’s agentic stack
AAIF gives these building blocks a neutral home and a path to evolve via open governance (technical steering, community input) — the same model the Linux Foundation has used to steward widely adopted infrastructure like Kubernetes and PyTorch. In parallel, complementary projects such as A2A and AGNTCY cover secure agent messaging, discovery and identity. Together, they point toward a layered, standards‑first approach: context and tool access (MCP), project guidance (AGENTS.md), execution frameworks (goose), secure messaging (A2A), and cross‑vendor discovery/identity (AGNTCY).
What changes now — and what you can do next
TipA 90‑day plan for builders
- Start standardizing on MCP for tool integrations; pilot against non‑critical systems first (e.g., read‑only connectors) before expanding.
- Add an AGENTS.md to your key repos so any compatible coding agent behaves consistently in CI/CD and local dev.
- Trial a local agent (e.g., goose) to automate repeatable engineering tasks; measure time‑to‑fix and rework rates.
- Establish guardrails early: code review for agent changes, least‑privilege credentials, and audit logs for tool execution.
- Track AAIF governance and specs; align with A2A/AGNTCY work for multi‑agent scenarios.
Open questions: security, identity and governance
More powerful agents expand the attack surface. With remote MCP servers now easy to deploy at the network edge, organizations need modern authN/authZ models, provenance, and isolation between agents and tools. Cloudflare’s recent release of a remote MCP server tier highlights the opportunity — and the need for careful security design.
Vendors are also moving identity controls into the agent era (for example, Microsoft Entra Agent ID for issuing governed identities to agents), but research continues to flag MCP‑specific risks (e.g., tool poisoning, weak server authentication) that enterprises should address with policy and testing. Expect AAIF to become a forum for shared safety patterns, secure defaults and maturity models as adoption scales.
Finally, governance matters. AAIF’s directed‑fund structure aims to encourage broad contribution without single‑vendor control, while still letting technical committees set roadmaps — a balance to watch as standards and implementations mature.
The bottom line
For teams investing in AI‑powered automation, AAIF is a pragmatic milestone: the most widely used agent standards and a credible reference framework are now under neutral stewardship. If your 2026 roadmap counts on agents doing real work — not just chat — adopting MCP and AGENTS.md, and experimenting with a framework like goose, will reduce integration friction today and future‑proof your stack for what’s coming next.
Sources
- OpenAI: Co‑founding the Agentic AI Foundation; donating AGENTS.md (Dec 9, 2025)
- Linux Foundation/AAIF press release: formation of AAIF; MCP, goose, AGENTS.md (Dec 9, 2025)
- Anthropic: Donating the Model Context Protocol to AAIF; adoption metrics (Dec 9, 2025)
- WIRED coverage of the AAIF launch and early backers (Dec 9, 2025)
- TechCrunch: Why Linux Foundation created AAIF; governance notes (Dec 9, 2025)
- Linux Foundation: Agent2Agent (A2A) protocol project (June 23, 2025)
- Linux Foundation: AGNTCY project announcement (July 29, 2025)
- Block’s goose framework (open source)
- Cloudflare: Remote MCP server and agent platform
- Microsoft Security Blog: Entra Agent ID and agent security